|
Monday, April 10, 2017
 Over and over recently we have seen small businesses come under attack from ransomware and viruses to phishing attempts. Don't think that just because you have a small business that you are free from the worry of a cyberattack. Around 40 Percent of cyberattacks specifically target small businesses according to the publication Small Business Trends. There are ways to combat cyberattacks and protect your business, whatever the size. Over and over recently we have seen small businesses come under attack from ransomware and viruses to phishing attempts. Don't think that just because you have a small business that you are free from the worry of a cyberattack. Around 40 Percent of cyberattacks specifically target small businesses according to the publication Small Business Trends. There are ways to combat cyberattacks and protect your business, whatever the size.
Read more . . .
Thursday, February 9, 2017
 Every day there are numerous phishing emails sent. You may have seen them in your daily email. But since phishing has been around for a long time, you think you know the signs or attributes of a phishing email and just delete them automatically. However, just as everything else has evolved over time, so has phishing. New kinds of attacks are on the rise including Spear Fishing which are emails targeted towards specific industries and some are so credible they often don't meet spam filter requirements and easily make it through to your inbox.
Read more . . .
Wednesday, January 25, 2017
 If you use WebEx's plugin on your Chrome browser you need to patch it now. If you happen to go to a URL that contains the string that WebEx uses to remotely start a meeting or visit your computer you may be in trouble. This string, if on a website you visit, can remotely execute code or command to allow an attacker access to your computer. An updated version of the plug-in for WebEx will roll out automatically. To check if you have the latest version, Go to your extensions page, If you have version 1.
Read more . . .
Thursday, December 8, 2016
 The Attorney General Eric T. Schneiderman has issued a consumer alert for attorneys specifically due to recent reports of a particular phishing scam that comes in the form of an email claiming that the firm is the subject of a complaint. The email includes a link to the complaint .Please warn your staff to NOT click on this link. Read more . . .
Tuesday, July 12, 2016
 The more sophisticated malware gets the more sophisticated your firewall has to be to fight it. WatchGuard has added APT (Advanced Persistent Threats) Blocker as another layer of prevention against advance ransomeware viruses that encrypt all of your data and make it inaccessible. APT blocker checks file against an existing database of malware. This happens first on the firewall itself and then in the cloud. If the file has never been seen before it is analyzed, and if found to be suspicious, blocked from ever entering your network. Read more . . .
Tuesday, June 14, 2016
 You, the CEO of a small business, are under attack. Right now, extremely dangerous and well-funded cybercrime rings in China, Russia and the Ukraine are using sophisticated software systems to hack into thousands of small businesses like yours to steal credit cards, client information, and swindle money directly out of your bank account. Some are even being funded by their own government to attack American businesses. Don’t think you’re in danger because you’re “small” and not a big target like a J.P. Read more . . .
Friday, April 15, 2016
 April's Patch Tuesday brings with it 6 fixes deemed critical and 7 that are marked important. One of these fixes MS16-039 is for Security Update for Microsoft Graphics Component (3148522) This security update resolves vulnerabilities in Microsoft Windows, Microsoft .NET Framework, Microsoft Office, Skype for Business, and Microsoft Lync. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a webpage that contains specially crafted embedded fonts. Other critical rated bulletins are MS16-037, MS16-038, MS16-040, MS16-042.
Read more . . .
Friday, April 15, 2016
 Apple thinks you should uninstall Quicktime for Windows as soon as possible. There are 2 reasons. 1) Apple is no longer going to be releasing any updates for this product for Windows 2) There are apparently 2 new vulnerabilities that Apple deemed critical enough that they released 2 advisories for recently. Those advisories would be ZDI-16-241 which allows remote attackers to execute code through Quicktime and Read more . . .
Thursday, March 24, 2016
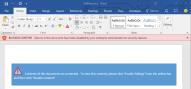 Some of the newer forms of malware coming into systems are macro-based. Recent data shows that 98 percent of Office targeted threats use macros. To combat this issue Microsoft has added into Office 2016 a feature that helps prevent the risk from macros and other higher risk scenarios. This feature can be set by group policy or allowing individual users rights to revise their settings. The thinking behind this is, if you block the macro, you block the threat. When you set your macro threshold lower, the user gets a warning when they try to open the email that states the contents of this document are being blocked. This feature relies on the security settings built into windows to specify trust. If the file originates from a location considered to be the internet zone the macros will be disabled. This helps cut down on malware getting through. It is not recommended that you enable macros on documents or emails from any source you do not trust or know. You should also be careful even with friends or colleagues as may have been unknowingly hacked. If it seems suspicious it probably is and it's best to heed the warnings. Any questions you may have regarding the disabling of macros, please contact us at Glasser Tech 516-762-0155.
Wednesday, March 23, 2016
 Apple has released it's iOS 9.3 which has some great new features for your iPhone and iPad. Some of these features include a Touch ID-secured version of notes and a new item thats called Night Shift that makes the display colors warmer and not so bright. Also included is a bug fix for a security hole, the possibility for third-party apps to add music to a user's iCloud Music library and 6s 3D touch functions. To update your phone, tap the settings icon, then go to general and then look for software update.
Wednesday, March 16, 2016
 Ransomeware is a malicous attack that causes your data to be unavailable to you unless you pay a payment to unlock the captive material. Often, ransomware requires that you pay this ransom in bitcoins. How does this happen? Malware can be delivered many different ways exploiting vulnerabilities through ad networks or older versions of a flash player.
According to "The Guardian," a news magazine, a number of major websites including the NLF, the New York Times, the BBC and AOL have all been hijacked. When a user visits a page that has been targeted, the page gets redirected to a different server hosting the malware. The malware then looks for any way to exploit the target computer. It installs a program similar to cryptolocker that takes over the user's data and encrypts it in such a way that you cannot use it again until you pay the ransom to get the information back. Ransomeware seems to be the newest trend for criminals versus the older forms of threats such as a virus, adware or trojans. It is best to keep your computer up to date with the most current Windows and Adobe updates as well as having an antivirus software such as Symantec Endpoint Cloud Protection which pushes new anti-virus signatures directly to your computer through the Cloud. If you have questions or concerns, we would be happy to assist you. Please contact Glasser Tech at 516-762-0155.
|
|
|
|